The Practical Benefits of a Unified Elasticsearch and Kibana Installation
Benefits of a Unified Elasticsearch & Kibana Setup from a Businesses standpoint
Get started with ReadonlyREST Enterprise and SAML in a localhost testbed

bin/standalone -b 0.0.0.0./bin/add-user-keycloak.sh -r master -u admin -p adminror realmror client of type SAML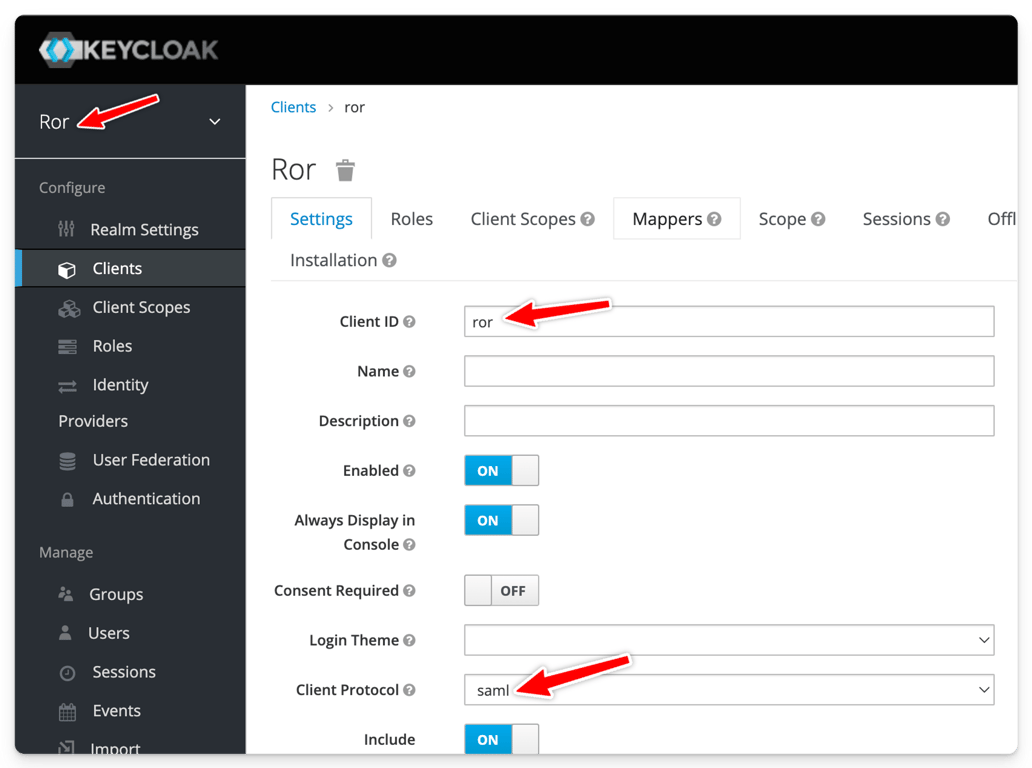
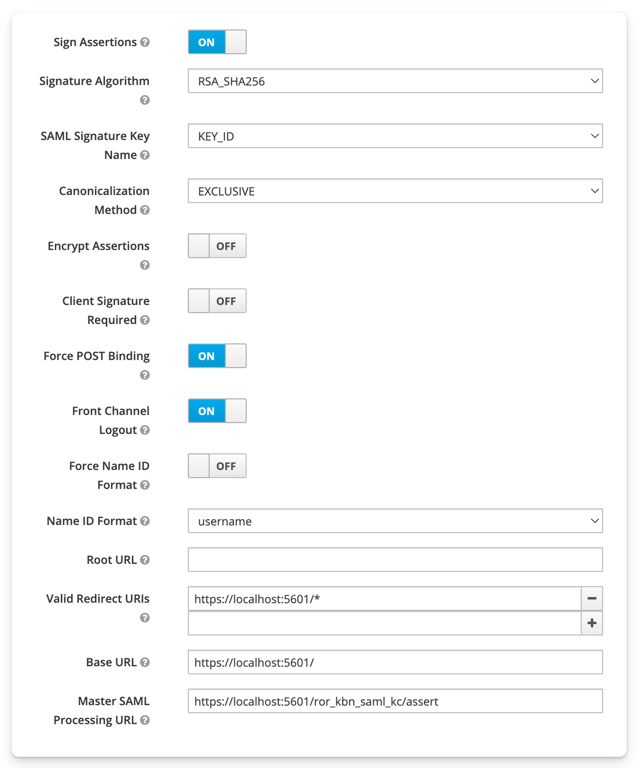
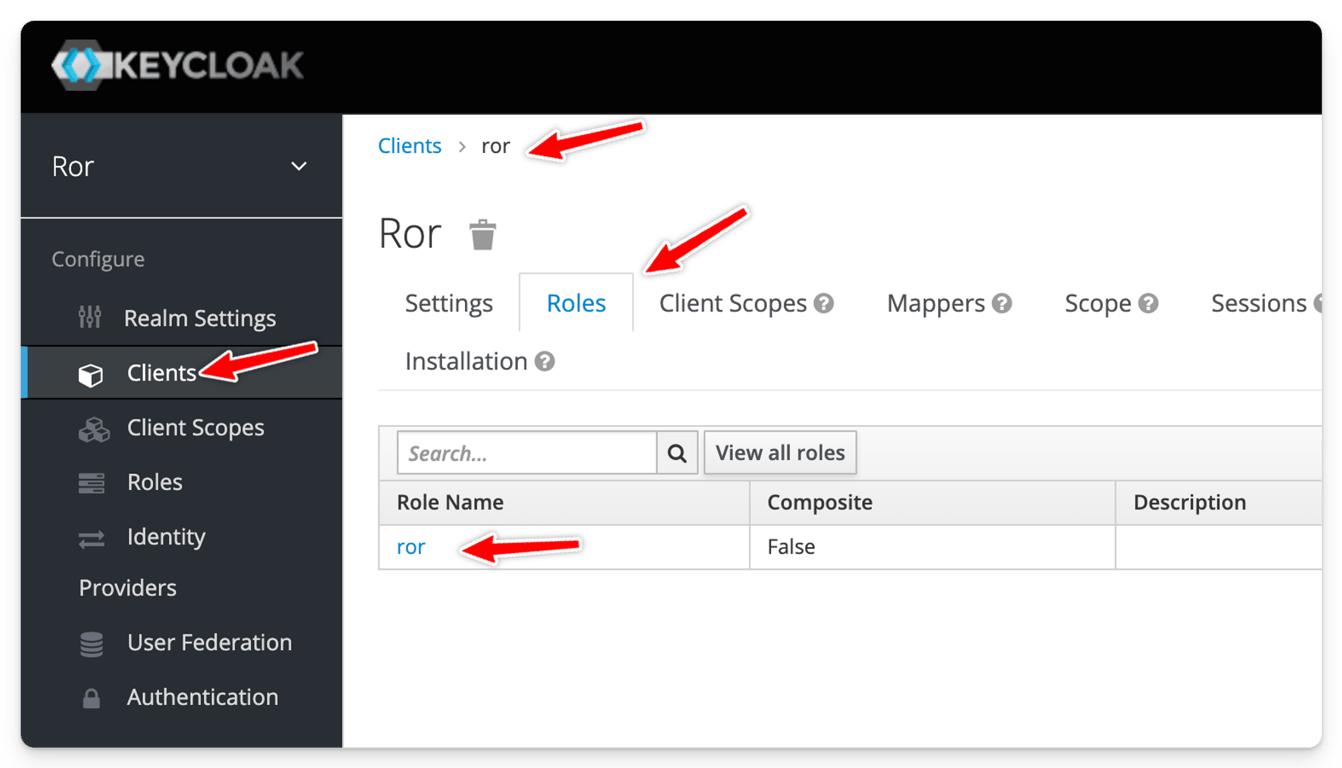
ror” name and make sure you have at least a user associated to it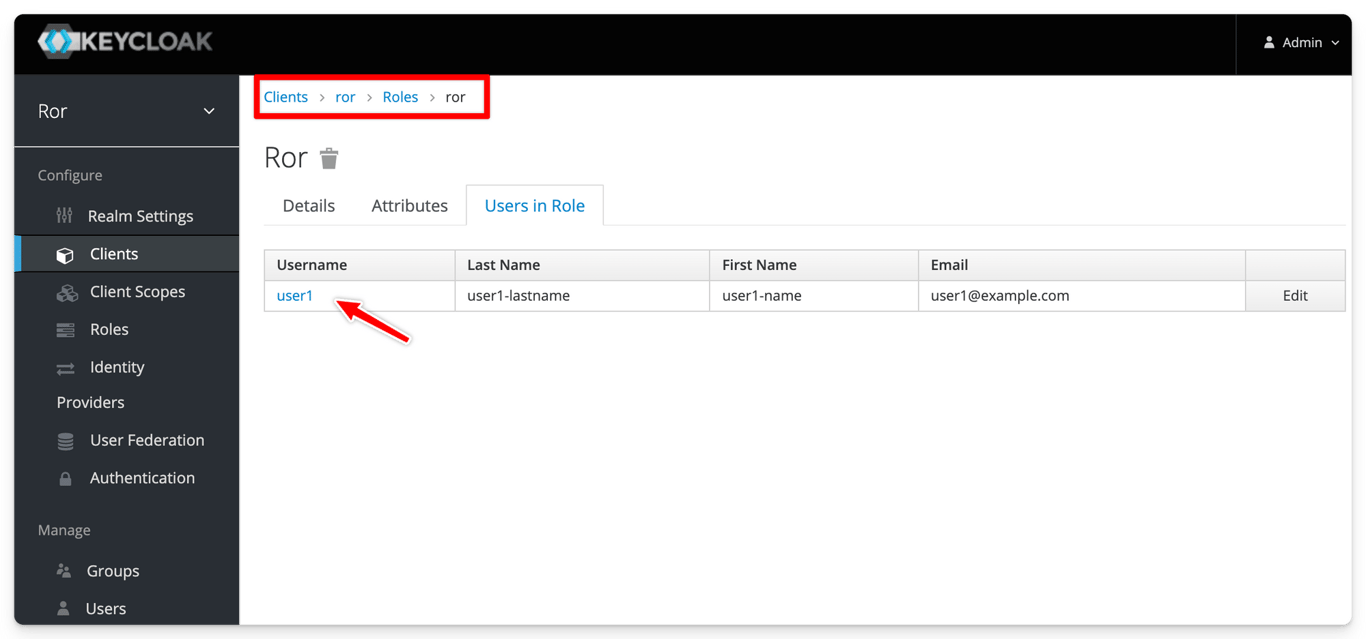
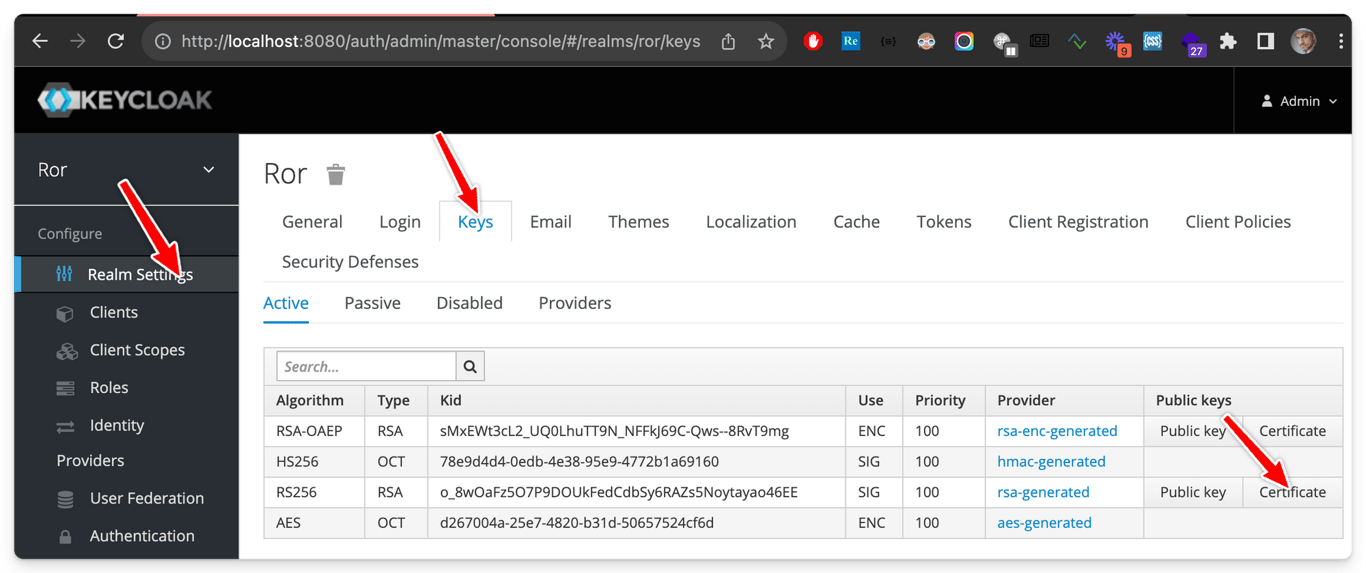
kibana.yml file in the “cert” field.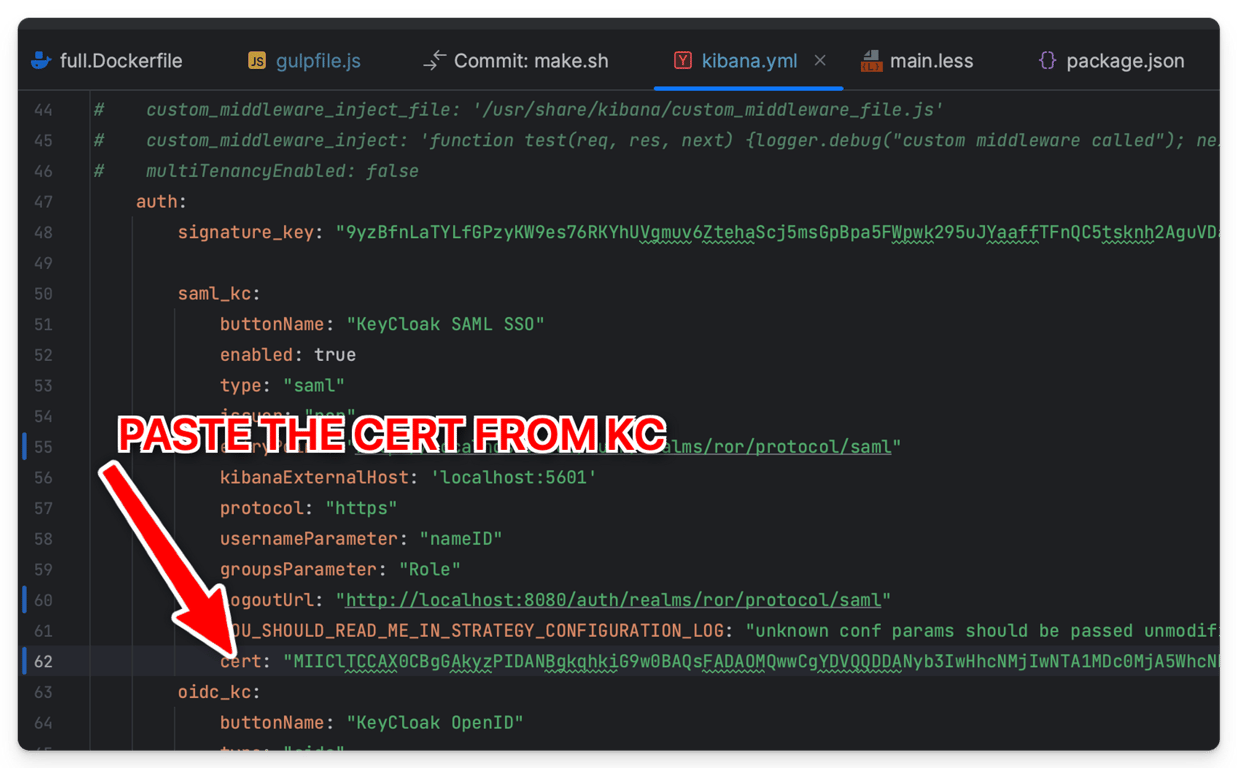
readonlyrest_kbn: cookiePass: '12312313123213123213123adadasdasdasd' logLevel: 'trace' clearSessionOnEvents: [login, tenancyHop] auth: signature_key: "9yzBfnLaTYLfGPzyKW9es76RKYhUVgmuv6ZtehaScj5msGpBpa5FWpwk295uJYaaffTFnQC5tsknh2AguVDaTrqCLfM5zCTqdE4UGNL73h28Bg4dPrvTAFQyygQqv4xfgnevBED6VZYdfjXAQLc8J8ywaHQQSmprZqYCWGE6sM3vzNUEWWB3kmGrEKa4sGbXhmXZCvL6NDnEJhXPDJAzu9BMQxn8CzVLqrx6BxDgPYF8gZCxtyxMckXwCaYXrxAGbjkYH69F4wYhuAdHSWgRAQCuWwYmWCA6g39j4VPge5pv962XYvxwJpvn23Y5KvNZ5S5c6crdG4f4gTCXnU36x92fKMQzsQV9K4phcuNvMWkpqVB6xMA5aPzUeHcGytD93dG8D52P5BxsgaJJE6QqDrk3Y2vyLw9ZEbJhPRJxbuBKVCBtVx26Ldd46dq5eyyzmNEyQGLrjQ4qd978VtG8TNT5rkn4ETJQEju5HfCBbjm3urGLFVqxhGVawecT4YM9Rry4EqXWkRJGTFQWQRnweUFbKNbVTC9NxcXEp6K5rSPEy9trb5UYLYhhMJ9fWSBMuenGRjNSJxeurMRCaxPpNppBLFnp8qW5ezfHgCBpEjkSNNzP4uXMZFAXmdUfJ8XQdPTWuYfdHYc5TZWnzrdq9wcfFQRDpDB2zX5Myu96krDt9vA7wNKfYwkSczA6qUQV66jA8nV4Cs38cDAKVBXnxz22ddAVrPv8ajpu7hgBtULMURjvLt94Nc5FDKw79CTTQxffWEj9BJCDCpQnTufmT8xenywwVJvtj49yv2MP2mGECrVDRmcGUAYBKR8G6ZnFAYDVC9UhY46FGWDcyVX3HKwgtHeb45Ww7dsW8JdMnZYctaEU585GZmqTJp2LcAWRcQPH25JewnPX8pjzVpJNcy7avfA2bcU86bfASvQBDUCrhjgRmK2ECR6vzPwTsYKRgFrDqb62FeMdrKgJ9vKs435T5ACN7MNtdRXHQ4fj5pNpUMDW26Wd7tt9bkBTqEGf" saml_kc: buttonName: "KeyCloak SAML SSO" enabled: true type: "saml" issuer: "ror" entryPoint: "http://localhost:8080/auth/realms/ror/protocol/saml" kibanaExternalHost: 'localhost:5601' protocol: "https" usernameParameter: "nameID" groupsParameter: "Role" logoutUrl: "http://localhost:8080/auth/realms/ror/protocol/saml" cert: "MIIClTCCAX0CBgGAkyzPIDANBgkqhkiG9w0BAQsFADAOMQwwCgYDVQQDDANyb3IwHhcNMjIwNTA1MDc0MjA5WhcNMzIwNTA1MDc0MzQ5WjAOMQwwCgYDVQQDDANyb3IwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCigkWUUB/kHBe76u6CxDK/W2kbqCfcZbWrCrMpQH5ESQC5YqG/WzObusaw5lWiGThzqJPFVXxbDnS+uh56ROw27TpxsSMwgyD2GpW42yl2G0Jrf3HYKskmFnrcy2PMTml8DbyGC3v59RRxVv2XR32cE3BeiID4WFhIcsWjrKTjB+0U+rhrocRXG+dalxiT0dyE1wgwkcEGCZu8vnKRYmC5sazw9xDWAZVcN+SKQweRMWu4ZO6TcrtIERT8NrswUlqij0c1VbmmC3qraK5Lmfn8QCE7ZDH17o8n8HyGBoETnQUHcfL9fFHF/cD/+CnjWocBAX0rjLBnl5S3IuaWT78xAgMBAAEwDQYJKoZIhvcNAQELBQADggEBAIgtUSteWw6ZVlpfV5ATkF1o9ZPcJj4KZ+BNfcB5UIcCPCONvO3GiHskCbHTSFSFtBEaxe1mLb2MEptqG0OVDOUtZtoOqWIc2KIObzkgBtOmLmt/modDlRbTzeoNwV4oiwz36VvoY1urxJYglUzQMQVJhEYPw5sxb/Yxj/4nUSgtF9ohVsEJCa0N+WSSykT87M1Afm/kKOO8hS7iGv7+SpSHfAXKQBHXQ4cLOuLoAs6OPPO0/U+XTdvEchXIrh24VPJAG+i5Y/kPkFbQciw8ULpMmwCSWH8W5vXAUfQMSJ47UkfD3TpzAZKNeSVGtwWv6i0EUrpXoPNC/+yuPuTWoQg="
readonlyrest.yml (on the Elasticsearch side) should contain a ror_kbn definition and a specific ACL block using it.readonlyrest: access_control_rules: - name: "ReadonlyREST Enterprise instance #1" kibana_index: ".kibana_external_auth" ror_kbn_auth: name: "kbn1" ror_kbn: - name: kbn1 signature_key: "9yzBfnLaTYLfGPzyKW9es76RKYhUVgmuv6ZtehaScj5msGpBpa5FWpwk295uJYaaffTFnQC5tsknh2AguVDaTrqCLfM5zCTqdE4UGNL73h28Bg4dPrvTAFQyygQqv4xfgnevBED6VZYdfjXAQLc8J8ywaHQQSmprZqYCWGE6sM3vzNUEWWB3kmGrEKa4sGbXhmXZCvL6NDnEJhXPDJAzu9BMQxn8CzVLqrx6BxDgPYF8gZCxtyxMckXwCaYXrxAGbjkYH69F4wYhuAdHSWgRAQCuWwYmWCA6g39j4VPge5pv962XYvxwJpvn23Y5KvNZ5S5c6crdG4f4gTCXnU36x92fKMQzsQV9K4phcuNvMWkpqVB6xMA5aPzUeHcGytD93dG8D52P5BxsgaJJE6QqDrk3Y2vyLw9ZEbJhPRJxbuBKVCBtVx26Ldd46dq5eyyzmNEyQGLrjQ4qd978VtG8TNT5rkn4ETJQEju5HfCBbjm3urGLFVqxhGVawecT4YM9Rry4EqXWkRJGTFQWQRnweUFbKNbVTC9NxcXEp6K5rSPEy9trb5UYLYhhMJ9fWSBMuenGRjNSJxeurMRCaxPpNppBLFnp8qW5ezfHgCBpEjkSNNzP4uXMZFAXmdUfJ8XQdPTWuYfdHYc5TZWnzrdq9wcfFQRDpDB2zX5Myu96krDt9vA7wNKfYwkSczA6qUQV66jA8nV4Cs38cDAKVBXnxz22ddAVrPv8ajpu7hgBtULMURjvLt94Nc5FDKw79CTTQxffWEj9BJCDCpQnTufmT8xenywwVJvtj49yv2MP2mGECrVDRmcGUAYBKR8G6ZnFAYDVC9UhY46FGWDcyVX3HKwgtHeb45Ww7dsW8JdMnZYctaEU585GZmqTJp2LcAWRcQPH25JewnPX8pjzVpJNcy7avfA2bcU86bfASvQBDUCrhjgRmK2ECR6vzPwTsYKRgFrDqb62FeMdrKgJ9vKs435T5ACN7MNtdRXHQ4fj5pNpUMDW26Wd7tt9bkBTqEGf"
signature_key fields have the same random value in both YAML files, so they share a secret and can validate the requests.